Basics of Computer Networking
Open system:
A system which is connected to the network and is ready for communication.
A system which is connected to the network and is ready for communication.
Closed system:
A system which is not connected to the network and can’t be communicated with.
A system which is not connected to the network and can’t be communicated with.
Computer Network:
It is the interconnection of multiple devices, generally termed as Hosts connected using multiple paths for the purpose of sending/receiving data or media.
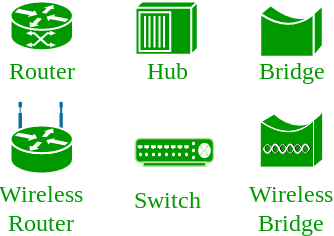
There are also multiple devices or mediums which helps in the communication between two different devices which are known as Network devices. Ex: Router, Switch, Hub, Bridge.
It is the interconnection of multiple devices, generally termed as Hosts connected using multiple paths for the purpose of sending/receiving data or media.
There are also multiple devices or mediums which helps in the communication between two different devices which are known as Network devices. Ex: Router, Switch, Hub, Bridge.

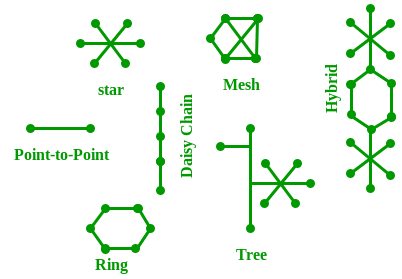
The layout pattern using which devices are interconnected is called as network topology. Such as Bus, Star, Mesh, Ring, Daisy chain.

OSI:
OSI stands for Open Systems Interconnection. It is a reference model that specifies standards for communications protocols and also the functionalities of each layer.
OSI stands for Open Systems Interconnection. It is a reference model that specifies standards for communications protocols and also the functionalities of each layer.
Protocol:
Protocol is the set of rules or algorthims which define the way how two entities can communicate across the network and there exists different protocol defined at each layer of OSI model. Few of such protocols are TCP, IP, UDP, ARP, DHCP, FTP and so on.
Protocol is the set of rules or algorthims which define the way how two entities can communicate across the network and there exists different protocol defined at each layer of OSI model. Few of such protocols are TCP, IP, UDP, ARP, DHCP, FTP and so on.
UNIQUE IDENTIFIERS OF NETWORK
Host name:
Each device in the network is associated with a unique device name known as Hostname.
Type “hostname” in the command prompt and press ‘Enter’, this displays the hostname of your machine.

Host name:
Each device in the network is associated with a unique device name known as Hostname.
Type “hostname” in the command prompt and press ‘Enter’, this displays the hostname of your machine.
IP Address (Internet Protocol address):
Also know as Logical Address, is the network address of the system across the network.
To identify each device in the world-wide web, Internet Assigned Numbers Authority (IANA) assigns IPV4 (Version 4) address as unique identifier for each device on the Internet.
Length of the IP address is : 32-bits. (Hence we have 232 ip addresses available.)
Type “ipconfig” in the command prompt and press ‘Enter’, this gives us the IP address of the device.
Also know as Logical Address, is the network address of the system across the network.
To identify each device in the world-wide web, Internet Assigned Numbers Authority (IANA) assigns IPV4 (Version 4) address as unique identifier for each device on the Internet.
Length of the IP address is : 32-bits. (Hence we have 232 ip addresses available.)
Type “ipconfig” in the command prompt and press ‘Enter’, this gives us the IP address of the device.
MAC Address (Media Access Control address):
Also known as physical address, is the unique identifier of each host and is associated with the NIC (Network Interface Card).
MAC address is assigned to the NIC at the time of manufacturing.
Length of the MAC address is : 12-nibble/ 6 bytes/ 48 bits
Type “ipconfig/all” in the command prompt and press ‘Enter’, this gives us the MAC address.
Also known as physical address, is the unique identifier of each host and is associated with the NIC (Network Interface Card).
MAC address is assigned to the NIC at the time of manufacturing.
Length of the MAC address is : 12-nibble/ 6 bytes/ 48 bits
Type “ipconfig/all” in the command prompt and press ‘Enter’, this gives us the MAC address.
Port:
Port can be referred as logical channel through which data can be sent/received to an application. Any host may have multiple applications running, and each of this application is identified using the port number on which they are running on.
Port number is a 16-bit integer, hence we have 216 ports available which are categorized as shown below:
Port can be referred as logical channel through which data can be sent/received to an application. Any host may have multiple applications running, and each of this application is identified using the port number on which they are running on.
Port number is a 16-bit integer, hence we have 216 ports available which are categorized as shown below:
| PORT TYPES | RANGE |
|---|---|
| Well known Ports | 0 – 1023 |
| Registered Ports | 1024 – 49151 |
| Ephemeral Ports | 49152 – 65535 |
Number of ports: 65,536
Range: 0 – 65535
Type “netstat -a” in the command prompt and press ‘Enter’, this lists all the ports being used.

Range: 0 – 65535
Type “netstat -a” in the command prompt and press ‘Enter’, this lists all the ports being used.
Socket:
The unique combination of IP address and Port number together are termed as Socket.
The unique combination of IP address and Port number together are termed as Socket.
Few more concepts
DNS Server:
DNS stands for Domain Name system.
DNS is basically a server which translate web addresses or URL (ex: www.google.com) into their corresponding IP addresses. We don’t have to remember all the IP addresses of each and every website.
The command ‘nslookup’ gives you the IP address of the domain you are looking for. This also provides the information of our DNS Server.

DNS Server:
DNS stands for Domain Name system.
DNS is basically a server which translate web addresses or URL (ex: www.google.com) into their corresponding IP addresses. We don’t have to remember all the IP addresses of each and every website.
The command ‘nslookup’ gives you the IP address of the domain you are looking for. This also provides the information of our DNS Server.
ARP:
ARP stands for Address Resolution Protocol.
It is used to convert the IP address to its corresponding Physical Address(i.e.MAC Address).
ARP is used by the Data Link Layer to identify the MAC address of the Receiver’s machine.
RARP:
RARP stands for Reverse Address Resolution Protocol.
As the name suggest, it provides the IP address of the a device given physical address as input. But RARP has become obsolete since the time DHCP has come into picture.
ARP stands for Address Resolution Protocol.
It is used to convert the IP address to its corresponding Physical Address(i.e.MAC Address).
ARP is used by the Data Link Layer to identify the MAC address of the Receiver’s machine.
RARP:
RARP stands for Reverse Address Resolution Protocol.
As the name suggest, it provides the IP address of the a device given physical address as input. But RARP has become obsolete since the time DHCP has come into picture.
The Internet and the Web
1. The Internet:
In simplest words it is a global network of smaller networks interconnected using communication protocols that are standardised. The Internet standards describe a framework known as the Internet protocol suite. This model divides methods into a layered system of protocols.
In simplest words it is a global network of smaller networks interconnected using communication protocols that are standardised. The Internet standards describe a framework known as the Internet protocol suite. This model divides methods into a layered system of protocols.
These layers are as follows:
- Application layer (highest) – concerned with the data(URL, type, etc), where HTTP, HTTPS, etc comes in.
- Transport layer – responsible for end-to-end communication over a network.
- Network layer – provides data route.
Provides a variety of information and communication facilities; contains forums, databases, email, hypertext, etc. It consists of private, public, academic, business, and government networks of local to global scope, linked by a broad array of electronic, wireless, and optical networking technologies.
2. The World Wide Web:
The web is a subset of the internet. It’s a system of Internet servers that support specially formatted documents. The documents are formatted in a markup language called HTML (that supports links, multimedia, etc). These documents are interlinked using hypertext links and are accessible via the Internet.
The web is a subset of the internet. It’s a system of Internet servers that support specially formatted documents. The documents are formatted in a markup language called HTML (that supports links, multimedia, etc). These documents are interlinked using hypertext links and are accessible via the Internet.
To link hypertext to the Internet, we need:
- The markup language, i.e., HTML.
- The transfer protocol, e.g., HTTP.
- Uniform Resource Locator (URL), the address of the resource.
We access the web using web browsers.
Difference between Web and Internet:
| INTERNET | WEB |
|---|---|
| Internet is the library and web a collection of books. The internet also consists of databases, email, forums, etc. | Web is a subset of the internet. The web is a large portion of the internet but it isn’t all of it. |
| The internet is a network, a way of transporting content and web lets us use that content. | The Web is ideally a way of accessing information over the medium of the Internet. Web is a collection of internet servers that can host HTML formatted documents. A collection of pages, of information connected to each other around the globe. Each page can be a combination of text and multimedia. |
URI:
URI stands for ‘Uniform Resource Identifier’, it’s like an address providing a unique global identifier to a resource on the Web. Uniform Resource Locator (URL) is the most commonly used form of a URI.
URI stands for ‘Uniform Resource Identifier’, it’s like an address providing a unique global identifier to a resource on the Web. Uniform Resource Locator (URL) is the most commonly used form of a URI.
The URL consists mainly of two parts:
- The protocol used in transfer, e.g., HTTP.
- The domain name.
Who governs the Internet?
The Internet is not governed, it has no single authority figure. The ultimate authority for where the Internet is going rests with the Internet Society, or ISOC.
ISOC is a voluntary membership organization whose purpose is to promote global information exchange through Internet technology.
The Internet is not governed, it has no single authority figure. The ultimate authority for where the Internet is going rests with the Internet Society, or ISOC.
ISOC is a voluntary membership organization whose purpose is to promote global information exchange through Internet technology.
- ISOC appoints the IAB- Internet Architecture Board. They meet regularly to review standards and allocate resources, like addresses.
- IETF- Internet Engineering Task Force. Another volunteer organisation that meets regularly to discuss operational and technical problems.
Internet and Web programming: Behind the scenes
Internet is the network of computers which connects the whole world together.But, how it actually work at the very low level?
Client side:
First when we type a url like www.google.com, the browser converts it into a file containing:
First when we type a url like www.google.com, the browser converts it into a file containing:
- GET /HTTP/1.1 (where GET means we are requesting some data from server and HTTP refers to protocol that we are using, 1.1 refers to version of HTTP request)
- Host: www.google.com
- And some other information
Now this file is converted to binary codes by the browser and send to the wires if we are connected through Ethernet and if we are using WiFi, it first converts to radio signal which is decoded by router and in the low level. It is converted to binary and sent to servers.
This information or simply binary codes goto the destination and respond is received by the sender only because of IP address.
One router send the information to another and this keep on going until the binary codes reaches the destination.
Server side:
Now the server receives the binary code and decode it and send the response in following manner:
Now the server receives the binary code and decode it and send the response in following manner:
- HTTP/1.1 200 ok (where 200 ok is the status)
- Content-type:type/html
- Body of page
Now this is converted back to binary by the server and sent to the IP address that is requesting it. Once this codes are received by the client, the browser again decode the information in following way:
- First it checks the status
- It starts reading the document from html tag and constructs Tree like structure.
- The html tree is then converted to corresponding binary code and rendered on the screen.
- In the end we see the website front-end.
Below is the tree structure of html document:

The following diagram show the whole process:

To understand the basic web terminology refer: The Internet and the Web
The New Internet | Internet of Everything
Internet Of Everything (IoE) has been the one of the trendiest topic lately and it’s here, IoE is the upcoming most innovative and Ubiquitous technology advancement which is going to make networked connections more relevant and valuable than ever before. Turning information into action that creates new capabilities, richer experiences and unprecedented economic opportunities for businesses, individuals and countries.
Technically IoE refers to billions of devices and consumer products connected to the internet in an intelligent networked environment with expanded digital features.
It is basically a philosophy in which our technology future is compromised of different types of appliances, devices, and things connected to the global internet.
As of now the internet connection is only restricted to Phone’s/Tablet’s, PC’s and a handful of other devices but the idea behind IoE is that in the future, Machines will become more intelligent and cognitive by having more access to data and expanded network opportunities.
As of now the internet connection is only restricted to Phone’s/Tablet’s, PC’s and a handful of other devices but the idea behind IoE is that in the future, Machines will become more intelligent and cognitive by having more access to data and expanded network opportunities.
In simpler terms IoE is the intelligent connection of people, process, data and things that will be transforming our world in such a way that there will be billions of connected devices having sensors to detect, measure and access their status all of which will be connected over public or private network built over standard protocols like TCP/IP.
So how is the; Internet of Everything any different from the Internet of Things?
Well, the difference is the intelligent connection. IoT is mostly about physical devices and objects communicating with each other but IoE brings with it the network intelligence to bind all these concepts together into a cohesive system.
Well, the difference is the intelligent connection. IoT is mostly about physical devices and objects communicating with each other but IoE brings with it the network intelligence to bind all these concepts together into a cohesive system.
IOT has been limited to only machines thus achieving Machine to Machine Communication but IoE brings together people, process, data, and things and adds them into the network therefore not just Phone’s/Tablet’s and PC’s but People. Health Fitness band’s, Coffee Pot’s, Marine Container’s all become a Node in an intelligent network communicating with each other. The more expansive IoE concepts include, besides M2M communication, M2P, and technology-assisted P2P communication.
The IoE Economy will profoundly effect four major Aspects of our lives:
- People –
People will be connected to the internet in more relevant ways and will be generating data and interacting with devices by not only through Mobile’s/Tablet’s, PC’s and Social Network but also through Sensors placed on human skins or sewn into clothing which will provide a person’s vital signs. In this way, people will themselves becomes Nodes on the internet.A good example is Nike’s wearable fitness band’s which read a person’s vital signs and sports apparel’s and gears embedded with chips which track the performance of Athletes. - Things –
Things and physical items such as sensors, industry devices, consumer products, enterprise assets will be connected to the internet or to each other, also fetching information from its surrounding’s, will be more context-aware, more cognitive, more intelligent, often so-called the internet of things.As of 1984, only 1000 devices were connected to the internet which increased to about 1 million in 1992 and shot across 10 Billion in 2010 and as Cisco predicts there will be around 50 Billion devices connected to the internet by 2020. These devices will be fetching data from its environment internally or externally and sending it back to the server for analyzing and making much more intelligent decisions. - Data –
Rather than simply collection Raw data, these connected devices will be sending higher level, more processed data back to respective servers for faster evaluation or more intelligent decision making.Here the data is more about insightful information and action plan than just random chunk. Figuring out a way to decipher the right flow of information is the key to making the best use of Big Data and as the types of data and sources increase, in order to draw useful insight’s there will be a need to classify information and analyze it. - Process –
With the equivalent to IOE process, the right information will be delivered to the right person at the right time in an appropriate way.
Technology-based Businesses will be relying on data to make further decisions and advance their workflow processes and strategies and will be therefore competing to leverage the data faster than their competitors for an agile and faster decision making.
General Electrics predicts that IoE can add 15 trillion dollars to the Global Domestic Product while Cisco estimates 19 trillion in savings and profits for companies that can leverage IoE. But as the number of devices connected to the internet increase and therefore collect more data, privacy is put at risk which increases security concerns but as these devices grow more intelligent, hopes is that the device and network will grow knowledgeable enough to detect, stop and prevent any harmful threats. IoE is here and is inevitable, we should embrace ourselves to adapt our lives to the changes that it brings with it.
Unknown facts of Networking
Some interesting facts about computer networking are:
- Internet was invented by Tim Berners-Lee in 1989.
- Internet is controlled by 75 million servers.
- Backbone of internet is made by 550, 000 miles of underwater cable.
- About one billion computer systems are connected to internet.
- About 3.2 billion people use the internet from which 1.7 billion internet users are Asians.
- Internet consists of five billion computing devices such as computers, phones, modems, switches, routers etc.
- According to Google, Internet consists of 5 million Terabytes of data.
- If the internet goes down for a day, approximately 200 billion emails and 3 billion Google search would have to wait.
- Approximately 204 million emails per minute are send over Internet. 70% of them are spam.
- 269 billion emails are sent per day.
- 30, 000 websites are hacked every day.
- 50 million horsepower is required by the internet to keep running in the current state.
- Approximately 9 million adults in Britain and 1/3rd of italians have never used the internet while China has treatment camps for internet addicts.
- Microsoft has more servers than Google. Microsoft owns over one million servers while Google has 900, 000.
- Internet bots and malware generate 61.5% or nearly two-thirds of all the website traffic.
- Approximately 1.7 trillion euro dollar worth of funds is spent online.
- Tim Berners-Lee was knighted by Queen Elizabeth.
- An email takes around 2 billion electrons to produce.
- Online dating generates approximately $1 billion dollars every year.
- Qwerty was designed to slow you down so that keys would not jam.
Computer Network | Network goals
Computer Network means an interconnection of autonomous (standalone) computers for information exchange. The connecting media could be a copper wire, optical fiber, microwave or satellite.
Networking Elements – The computer network includes the following networking elements:
- At least two computers
- Transmission medium either wired or wireless
- Protocols or rules that govern the communication
- Network software such as Network Operating System
Network Criteria:
The criteria that have to be met by a computer network are:
The criteria that have to be met by a computer network are:
1. Performance – It is measured in terms of transit time and response time.
- Transit time is the time for a message to travel from one device to another
- Response time is the elapsed time between an inquiry and a response.
Performance is dependent on the following factors:
- The number of users
- Type of transmission medium
- Capability of connected network
- Efficiency of software
2. Reliability – It is measured in terms of
- Frequency of failure
- Recovery from failures
- Robustness during catastrophe
3. Security – It means protecting data from unauthorized access.
Goals of Computer Networks: The following are some important goals of computer networks:
Goals of Computer Networks: The following are some important goals of computer networks:
- Resource Sharing –
Many organization has a substantial number of computers in operations, which are located apart. Ex. A group of office workers can share a common printer, fax, modem, scanner etc. - High Reliability –
If there are alternate sources of supply, all files could be replicated on two or, machines. If one of them is not available, due to hardware failure, the other copies could be used. - Inter-process Communication –
Network users, located geographically apart, may converse in an interactive session through the network. In order to permit this, the network must provide almost error-free communications. - Flexible access –
Files can be accessed from any computer in the network. The project can be begun on one computer and finished on another.
Other goals include Distribution of processing functions, Centralized management, and allocation of network resources, Compatibility of dissimilar equipment and software, Good network performance, Scalability, Saving money, Access to remote information, Person to person communication etc.,
Line Configuration in Computer Networks
A network is two or more devices connected through a link. A link is a communication pathway that transfer data from one device to another. Devices can be a computer, printer or any other device that is capable to send and receive data. For visualization purpose, imagine any link as a line drawn between two points.
For communication to occur, two devices must be connected in some way to the same link at the same time. There are two possible types of connections:
For communication to occur, two devices must be connected in some way to the same link at the same time. There are two possible types of connections:
- Point-to-Point Connection
- Multipoint Connection
Point-to-Point Connection :
- A point-to-point connection provides a dedicated link between two devices.
- The entire capacity of the link is reserved for transmission between those two devices.
- Most point-to-point connections use a actual length of wire or cable to connect the two end, but other options such as microwave or satellite links are also possible.
- Point to point network topology is considered to be one of the easiest and most conventional network
topologies. - It is also the simplest to establish and understand.
Example: Point-to-Point connection between remote control and Television for changing the channels.

Multipoint Connection :
- It is also called Multidrop configuration. In this connection two or more devices share a single link.
- More than two devices share the link that is the capacity of the channel is shared now. With shared capacity, there can be two possibilities in a Multipoint Line configuration:
Spatial Sharing: If several devices can share the link simultaneously, its called Spatially shared line configuration.
Temporal (Time) Sharing: If users must take turns using the link , then its called Temporally shared or Time Shared Line configuration.
Temporal (Time) Sharing: If users must take turns using the link , then its called Temporally shared or Time Shared Line configuration.

References : http://mucins.weebly.com/21-line-configuration.html
Transmission Modes in Computer Networks (Simplex, Half-Duplex and Full-Duplex)
Transmission mode means transferring of data between two devices. It is also known as communication mode. Buses and networks are designed to allow communication to occur between individual devices that are interconnected. There are three types of transmission mode:-

Simplex Mode
In Simplex mode, the communication is unidirectional, as on a one-way street. Only one of the two devices on a link can transmit, the other can only receive. The simplex mode can use the entire capacity of the channel to send data in one direction.
Example: Keyboard and traditional monitors. The keyboard can only introduce input, the monitor can only give the output.

Half-Duplex Mode
In half-duplex mode, each station can both transmit and receive, but not at the same time. When one device is sending, the other can only receive, and vice versa. The half-duplex mode is used in cases where there is no need for communication in both direction at the same time. The entire capacity of the channel can be utilized for each direction.
Example: Walkie- talkie in which message is sent one at a time and messages are sent in both the directions.

Full-Duplex Mode
In full-duplex mode, both stations can transmit and receive simultaneously. In full_duplex mode, signals going in one direction share the capacity of the link with signals going in other direction, this sharing can occur in two ways:
In full-duplex mode, both stations can transmit and receive simultaneously. In full_duplex mode, signals going in one direction share the capacity of the link with signals going in other direction, this sharing can occur in two ways:
Full-duplex mode is used when communication in both direction is required all the time. The capacity of the channel, however must be divided between the two directions.
Example: Telephone Network in which there is communication between two persons by a telephone line, through which both can talk and listen at the same time.
Example: Telephone Network in which there is communication between two persons by a telephone line, through which both can talk and listen at the same time.

References- Data Communication and Network,5th Edition,Behrouz A.Forouzan.
Types of Transmission Media
In data communication terminology, a transmission medium is a physical path between the transmitter and the receiver i.e it is the channel through which data is sent from one place to another. Transmission Media is broadly classified into the following types:
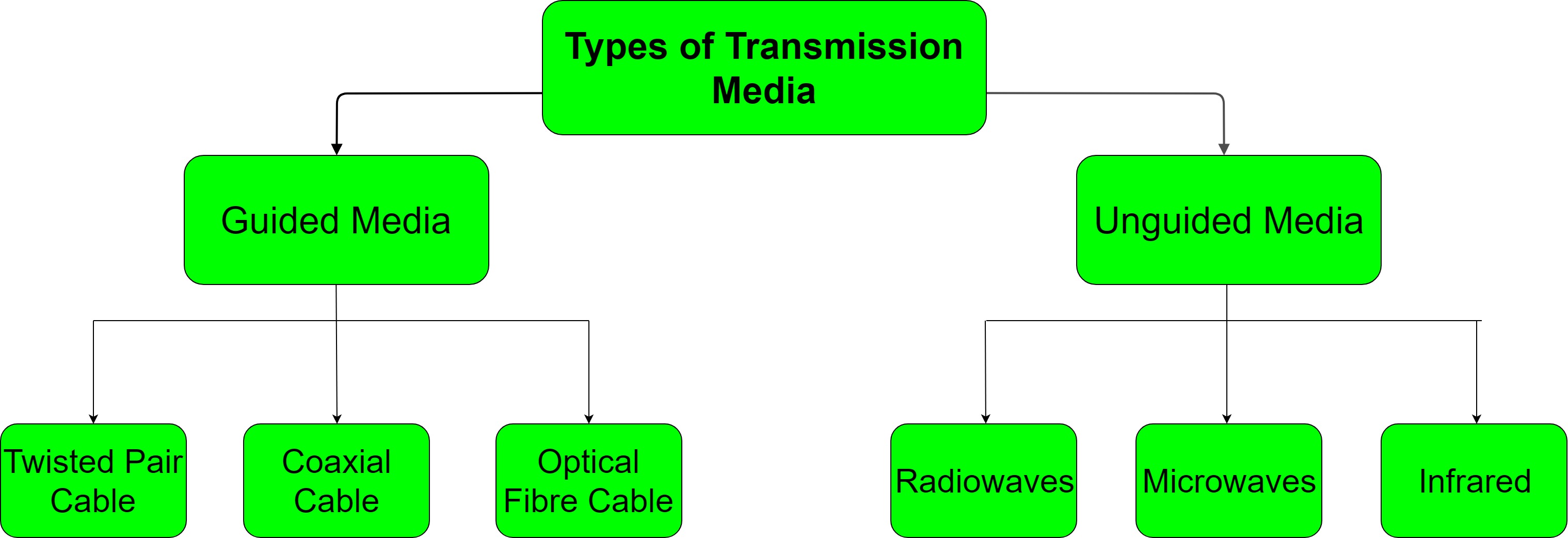
1. Guided Media:
It is also referred to as Wired or Bounded transmission media. Signals being transmitted are directed and confined in a narrow pathway by using physical links.
It is also referred to as Wired or Bounded transmission media. Signals being transmitted are directed and confined in a narrow pathway by using physical links.
Features:
- High Speed
- Secure
- Used for comparatively shorter distances
There are 3 major types of Guided Media:
(i) Twisted Pair Cable –
It consists of 2 separately insulated conductor wires wound about each other. Generally, several such pairs are bundled together in a protective sheath. They are the most widely used Transmission Media. Twisted Pair is of two types:
It consists of 2 separately insulated conductor wires wound about each other. Generally, several such pairs are bundled together in a protective sheath. They are the most widely used Transmission Media. Twisted Pair is of two types:
- Unshielded Twisted Pair (UTP):
This type of cable has the ability to block interference and does not depend on a physical shield for this purpose. It is used for telephonic applications.Advantages:- Least expensive
- Easy to install
- High speed capacity
Disadvantages:- Susceptible to external interference
- Lower capacity and performance in comparison to STP
- Short distance transmission due to attenuation
- Shielded Twisted Pair (STP):
This type of cable consists of a special jacket to block external interference. It is used in fast-data-rate Ethernet and in voice and data channels of telephone lines.Advantages:- Better performance at a higher data rate in comparison to UTP
- Eliminates crosstalk
- Comparitively faster
Disadvantages:- Comparitively difficult to install and manufacture
- More expensive
- Bulky
(ii) Coaxial Cable –
It has an outer plastic covering containing 2 parallel conductors each having a separate insulated protection cover. Coaxial cable transmits information in two modes: Baseband mode(dedicated cable bandwidth) and Broadband mode(cable bandwidth is split into separate ranges). Cable TVs and analog television networks widely use Coaxial cables.
It has an outer plastic covering containing 2 parallel conductors each having a separate insulated protection cover. Coaxial cable transmits information in two modes: Baseband mode(dedicated cable bandwidth) and Broadband mode(cable bandwidth is split into separate ranges). Cable TVs and analog television networks widely use Coaxial cables.
Advantages:
- High Bandwidth
- Better noise Immunity
- Easy to install and expand
- Inexpensive
Disadvantages:
- Single cable failure can disrupt the entire network
(iii) Optical Fibre Cable –
It uses the concept of reflection of light through a core made up of glass or plastic. The core is surrounded by a less dense glass or plastic covering called the cladding. It is used for transmission of large volumes of data.
It uses the concept of reflection of light through a core made up of glass or plastic. The core is surrounded by a less dense glass or plastic covering called the cladding. It is used for transmission of large volumes of data.
Advantages:
- Increased capacity and bandwidth
- Light weight
- Less signal attenuation
- Immunity to electromagnetic interference
- Resistance to corrosive materials
Disadvantages:
- Difficult to install and maintain
- High cost
- Fragile
- unidirectional, ie, will need another fibre, if we need bidirectional communication
2. Unguided Media:
It is also referred to as Wireless or Unbounded transmission media.No physical medium is required for the transmission of electromagnetic signals.
It is also referred to as Wireless or Unbounded transmission media.No physical medium is required for the transmission of electromagnetic signals.
Features:
- Signal is broadcasted through air
- Less Secure
- Used for larger distances
There are 3 major types of Unguided Media:
(i) Radiowaves –
These are easy to generate and can penetrate through buildings. The sending and receiving antennas need not be aligned. Frequency Range:3KHz – 1GHz. AM and FM radios and cordless phones use Radiowaves for transmission.
These are easy to generate and can penetrate through buildings. The sending and receiving antennas need not be aligned. Frequency Range:3KHz – 1GHz. AM and FM radios and cordless phones use Radiowaves for transmission.
Further Categorized as (i) Terrestrial and (ii) Satellite.
(ii) Microwaves –
It is a line of sight transmission i.e. the sending and receiving antennas need to be properly aligned with each other. The distance covered by the signal is directly proportional to the height of the antenna. Frequency Range:1GHz – 300GHz. These are majorly used for mobile phone communication and television distribution.
It is a line of sight transmission i.e. the sending and receiving antennas need to be properly aligned with each other. The distance covered by the signal is directly proportional to the height of the antenna. Frequency Range:1GHz – 300GHz. These are majorly used for mobile phone communication and television distribution.
(iii) Infrared –
Infrared waves are used for very short distance communication. They cannot penetrate through obstacles. This prevents interference between systems. Frequency Range:300GHz – 400THz. It is used in TV remotes, wireless mouse, keyboard, printer, etc.

IP : Internet Protocol
FTP : File Transfer Protocol
SMTP : Simple Mail Transfer Protocol
HTTP : Hyper Text Transfer Protocol






The functions of the physical layer are :
Infrared waves are used for very short distance communication. They cannot penetrate through obstacles. This prevents interference between systems. Frequency Range:300GHz – 400THz. It is used in TV remotes, wireless mouse, keyboard, printer, etc.
Computer Network | Difference between Unicast, Broadcast and Multicast
The cast term here signifies some data(stream of packets) is being transmitted to the recipient(s) from client(s) side over the communication channel that help them to communicate. Let’s see some of the “cast” concepts that are prevailing in the computer networks field.
1. Unicast –
This type of information transfer is useful when there is a participation of single sender and single recipient. So, in short you can term it as a one-to-one transmission. For example, a device having IP address 10.1.2.0 in a network wants to send the traffic stream(data packets) to the device with IP address 20.12.4.2 in the other network,then unicast comes into picture. This is the most common form of data transfer over the networks.

2. Broadcast –
Broadcasting transfer (one-to-all) techniques can be classified into two types :
- Limited Broadcasting –
Suppose you have to send stream of packets to all the devices over the network that you reside, this broadcasting comes handy. For this to achieve,it will append 255.255.255.255 (all the 32 bits of IP address set to 1) called as Limited Broadcast Address in the destination address of the datagram (packet) header which is reserved for information tranfer to all the recipients from a single client (sender) over the network.
- Direct Broadcasting –
This is useful when a device in one network wants to transfer packet stream to all the devices over the other network.This is achieved by translating all the Host ID part bits of the destination address to 1,referred as Direct Broadcast Address in the datagram header for information transfer.
This mode is mainly utilized by television networks for video and audio distribution.
One important protocol of this class in Computer Networks is Address Resolution Protocol (ARP) that is used for resolving IP address into physical address which is necessary for underlying communication.
One important protocol of this class in Computer Networks is Address Resolution Protocol (ARP) that is used for resolving IP address into physical address which is necessary for underlying communication.
3. Multicast –
In multicasting, one/more senders and one/more recipients participate in data transfer traffic. In this method traffic recline between the boundaries of unicast (one-to-one) and broadcast (one-to-all). Multicast lets server’s direct single copies of data streams that are then simulated and routed to hosts that request it. IP multicast requires support of some other protocols like IGMP (Internet Group Management Protocol), Multicast routing for its working. Also in Classful IP addressing Class D is reserved for multicast groups.
Questions Corner –
Practicing the following questions will help you test your knowledge. It is highly recommended that you practice them.
References –
Difference between Unicast, Broadcast and Multicast
erg.abdn.ac.uk
Difference between Unicast, Multicast, Broadcast
erg.abdn.ac.uk
Difference between Unicast, Multicast, Broadcast
Introduction to basic Networking terminology
For a specific purpose if things are connected together, are referred as a NETWORK. A network can be of many types, like a telephone network, television network, computer network or even a people network.
Similarly, a COMPUTER NETWORK is also a kind of setup, where it connects two or more devices to share a range of services and information in the form of e-mails and messages, databases, documents, web-sites, audios and videoes, Telephone calls and video conferences etc among them.
A PROTOCOL is nothing but set of defined rules, which has to be followed by every connected devices across a network to communicate and share information among them. To facilitates End to End communication, a number of protocols worked together to form a Protocol Suites or Stacks.
Some basic Protocols are:
Some basic Protocols are:
The Network reference models were developed to allow products from different manufacturers to interoperate on a network. A network reference model serves as a blueprint, detailing standards for how protocol communication should occur.
The most widely recognized reference models are, the Open Systems Interconnect ( OSI ) Model and Department of Defense ( DoD, also known as TCP/IP ) model.
The most widely recognized reference models are, the Open Systems Interconnect ( OSI ) Model and Department of Defense ( DoD, also known as TCP/IP ) model.
- Network Types are often categorized by their size and functionality. According to the size, the network can be commonly categorized into Three types.
- LANs (Local Area Networks)
- MANs (Metropolitan Area Networks)
- WANs (Wide Area Networks)
An Internetwork is a general term describing multiple networks connected together. The Internet is the largest and most well-known internetwork.
- SAN (Storage Area Network): A SAN provides systems with high-speed, lossless access to high-capacity storage devices.
- VPN (Virtual Private Network): A VPN allows for information to be securely sent across a public or unsecure network, such as the Internet. Common uses of a VPN are to connect branch offices or remote users to a main office.
Some networks are categorized by their function, as opposed to their size. For example:
- In a network, any connected device is called as host. A host can serve as following ways:
- A host can acts as a Client, when he is requesting information.
- A host can acts as a Server, when he provides information.
- A host can also request and provide information, is called Peer.
Network Topologies | Computer Networks
The arrangement of a network which comprises of nodes and connecting lines via sender and receiver is referred as network topology. The various network topologies are :
a) Mesh Topology :
In mesh topology, every device is connected to another device via particular channel.

Figure 1 : Every device is connected with another via dedicated channels. These channels are known as links.
- If suppose, N number of devices are connected with each other in mesh topology, then total number of ports that is required by each device is N-1. In the Figure 1, there are 5 devices connected to each other, hence total number of ports required is 4.
- If suppose, N number of devices are connected with each other in mesh topology, then total number of dedicated links required to connect them is NC2 i.e. N(N-1)/2. In the Figure 1, there are 5 devices connected to each other, hence total number of links required is 5*4/2 = 10.
Advantages of this topology :
- It is robust.
- Fault is diagnosed easily. Data is reliable because data is transferred among the devices through dedicated channels or links.
- Provides security and privacy.
Problems with this topology :
- Installation and configuration is difficult.
- Cost of cables are high as bulk wiring is required, hence suitable for less number of devices.
- Cost of maintenance is high.
b) Star Topology :
In star topology, all the devices are connected to a single hub through a cable. This hub is the central node and all others nodes are connected to the central node. The hub can be passive in nature i.e. not intelligent hub such as broadcasting devices, at the same time the hub can be intelligent known as active hubs. Active hubs have repeaters in them.

Figure 2 : A star topology having four systems connected to single point of connection i.e. hub.
Advantages of this topology :
Advantages of this topology :
- If N devices are connected to each other in star topology, then the number of cables required to connect them is N. So, it is easy to set up.
- Each device require only 1 port i.e. to connect to the hub.
Problems with this topology :
- If the concentrator (hub) on which the whole topology relies fails, the whole system will crash down.
- Cost of installation is high.
- Performance is based on the single concentrator i.e. hub.
c) Bus Topology :
Bus topology is a network type in which every computer and network device is connected to single cable. It transmits the data from one end to another in single direction. No bi-directional feature is in bus topology.

Figure 3 : A bus topology with shared backbone cable. The nodes are connected to the channel via drop lines.
Advantages of this topology :
Advantages of this topology :
- If N devices are connected to each other in bus topology, then the number of cables required to connect them is 1 which is known as backbone cable and N drop lines are required.
- Cost of the cable is less as compared to other topology, but it is used to built small networks.
Problems with this topology :
- If the common cable fails, then the whole system will crash down.
- If the network traffic is heavy, it increases collisions in the network. To avoid this, various protocols are used in MAC layer known as Pure Aloha, Slotted Aloha, CSMA/CD etc.
d) Ring Topology :
In this topology, it forms a ring connecting a devices with its exactly two neighbouring devices.

Figure 4 : A ring topology comprises of 4 stations connected with each forming a ring..
The following operations takes place in ring topology are :
The following operations takes place in ring topology are :
- One station is known as monitor station which takes all the responsibility to perform the operations.
- To transmit the data, station has to hold the token. After the transmission is done, the token is to be released for other stations to use.
- When no station is transmitting the data, then the token will circulate in the ring.
- There are two types of token release techniques : Early token release releases the token just after the transmitting the data and Delay token release releases the token after the acknowledgement is received from the receiver.
Advantages of this topology :
- The possibility of collision is minimum in this type of topology.
- Cheap to install and expand.
Problems with this topology :
- Troubleshooting is difficult in this topology.
- Addition of stations in between or removal of stations can disturb the whole topology.
e) Hybrid Topology :
This topology is a collection of two or more topologies which are described above. This is a scalable topology which can be expanded easily. It is reliable one but at the same it is a costly topology.

Figure 5 : A hybrid topology which is a combination of ring and star topology.
Computer Network | Types of area networks – LAN, MAN and WAN
The Network allows computers to connect and communicate with different computers via any medium. LAN, MAN and WAN are the three major types of the network designed to operate over the area they cover. There are some similarities and dissimilarities between them. One of the major differences is the geographical area they cover, i.e. LAN covers the smallest area; MAN covers an area larger than LAN and WAN comprises the largest of all.
There are other types of Computer Networks also, like :
There are other types of Computer Networks also, like :
- PAN (Personal Area Network)
- SAN (Storage Area Network)
- EPN (Enterprise Private Network)
- VPN (Virtual Private Network)
Local Area Network (LAN) –
LAN or Local Area Network connects network devices in such a way that personal computer and workstations can share data, tools and programs. The group of computers and devices are connected together by a switch, or stack of switches, using a private addressing scheme as defined by the TCP/IP protocol. Private addresses are unique in relation to other computers on the local network. Routers are found at the boundary of a LAN, connecting them to the larger WAN.
LAN or Local Area Network connects network devices in such a way that personal computer and workstations can share data, tools and programs. The group of computers and devices are connected together by a switch, or stack of switches, using a private addressing scheme as defined by the TCP/IP protocol. Private addresses are unique in relation to other computers on the local network. Routers are found at the boundary of a LAN, connecting them to the larger WAN.
Data transmits at a very fast rate as the number of computers linked are limited. By definition, the connections must be high speed and relatively inexpensive hardware (Such as hubs, network adapters and Ethernet cables). LANs cover smaller geographical area (Size is limited to a few kilometers) and are privately owned. One can use it for an office building, home, hospital, schools, etc. LAN is easy to design and maintain. A Communication medium used for LAN has twisted pair cables and coaxial cables. It covers a short distance, and so the error and noise are minimized.
Early LAN’s had data rates in the 4 to 16 Mbps range. Today, speeds are normally 100 or 1000 Mbps. Propagation delay is very short in a LAN. The smallest LAN may only use two computers, while larger LANs can accommodate thousands of computers. A LAN typically relies mostly on wired connections for increased speed and security, but wireless connections can also be part of a LAN. The fault tolerance of a LAN is more and there is less congestion in this network. For example : A bunch of students playing Counter Strike in the same room (without internet).
Metropolitan Area Network (MAN) –
MAN or Metropolitan area Network covers a larger area than that of a LAN and smaller area as compared to WAN. It connects two or more computers that are apart but resides in the same or different cities. It covers a large geographical area and may serve as an ISP (Internet Service Provider). MAN is designed for customers who need a high-speed connectivity. Speeds of MAN ranges in terms of Mbps. It’s hard to design and maintain a Metropolitan Area Network.
MAN or Metropolitan area Network covers a larger area than that of a LAN and smaller area as compared to WAN. It connects two or more computers that are apart but resides in the same or different cities. It covers a large geographical area and may serve as an ISP (Internet Service Provider). MAN is designed for customers who need a high-speed connectivity. Speeds of MAN ranges in terms of Mbps. It’s hard to design and maintain a Metropolitan Area Network.
The fault tolerance of a MAN is less and also there is more congestion in the network. It is costly and may or may not be owned by a single organization. The data transfer rate and the propagation delay of MAN is moderate. Devices used for transmission of data through MAN are: Modem and Wire/Cable. Examples of a MAN are the part of the telephone company network that can provide a high-speed DSL line to the customer or the cable TV network in a city.
Wide Area Network (WAN) –
WAN or Wide Area Network is a computer network that extends over a large geographical area, although it might be confined within the bounds of a state or country. A WAN could be a connection of LAN connecting to other LAN’s via telephone lines and radio waves and may be limited to an enterprise (a corporation or an organization) or accessible to the public. The technology is high speed and relatively expensive.
WAN or Wide Area Network is a computer network that extends over a large geographical area, although it might be confined within the bounds of a state or country. A WAN could be a connection of LAN connecting to other LAN’s via telephone lines and radio waves and may be limited to an enterprise (a corporation or an organization) or accessible to the public. The technology is high speed and relatively expensive.
There are two types of WAN: Switched WAN and Point-to-Point WAN. WAN is difficult to design and maintain. Similar to a MAN, the fault tolerance of a WAN is less and there is more congestion in the network. A Communication medium used for WAN is PSTN or Satellite Link. Due to long distance transmission, the noise and error tend to be more in WAN.
WAN’s data rate is slow about a 10th LAN’s speed, since it involves increased distance and increased number of servers and terminals etc. Speeds of WAN ranges from few kilobits per second (Kbps) to megabits per second (Mbps). Propagation delay is one of the biggest problems faced here. Devices used for transmission of data through WAN are: Optic wires, Microwaves and Satellites. Example of a Switched WAN is the asynchronous transfer mode (ATM) network and Point-to-Point WAN is dial-up line that connects a home computer to the Internet.
Conclusion –
There are many advantages of LAN over MAN and WAN, such as LAN’s provide excellent reliability, high data transmission rate, they can easily be managed, and shares peripheral devices too. Local Area Network cannot cover cities or towns and for that Metropolitan Area Network is needed, which can connect city or a group of cities together. Further, for connecting Country or a group of Countries one requires Wide Area Network.
There are many advantages of LAN over MAN and WAN, such as LAN’s provide excellent reliability, high data transmission rate, they can easily be managed, and shares peripheral devices too. Local Area Network cannot cover cities or towns and for that Metropolitan Area Network is needed, which can connect city or a group of cities together. Further, for connecting Country or a group of Countries one requires Wide Area Network.
Telecom Networks
Telecom networks is mostly used today for wide area communication. Stringing a wire between every pair of telephones that might want to communicate was not a good long term strategy. A better idea was to connect all the telephones to a central switching office. There an operator could connect one telephone to another via a switch board.
Routing a telephone call:
A call is routed up through higher level switching offices until it reaches a switching office that can reach the destination telephone by connecting with lower level switching offices, which examine the digits of the telephone number you dialled to make these decisions.
A call is routed up through higher level switching offices until it reaches a switching office that can reach the destination telephone by connecting with lower level switching offices, which examine the digits of the telephone number you dialled to make these decisions.
Connection Oriented Services – I :
A dedicated connection between the end points are maintained throughout the session. Usually, this means that the quality of service can be reasonably guaranteed to the extent of the bandwidth for the channel that is established. Message bits arrive in the same order in which they are sent. Traditional telephone circuit is a circuit switched connection oriented system.
A dedicated connection between the end points are maintained throughout the session. Usually, this means that the quality of service can be reasonably guaranteed to the extent of the bandwidth for the channel that is established. Message bits arrive in the same order in which they are sent. Traditional telephone circuit is a circuit switched connection oriented system.
Transmission Media in Telephone Systems:
In traditional analogue telephone systems, the telephone is connected to the local exchange via category 3 UTP cables. This connection is called the local loop. It is typically between 1km and 10km length. Higher up in the hierarchy, higher bandwidth cables are used to carry multiple telephone calls. This is far cheaper than using separate cables for separate calls. Specifically, digital lines on fiber is used. Analogue systems used a technique called frequency division multiplexing (FDM) to do this.
In traditional analogue telephone systems, the telephone is connected to the local exchange via category 3 UTP cables. This connection is called the local loop. It is typically between 1km and 10km length. Higher up in the hierarchy, higher bandwidth cables are used to carry multiple telephone calls. This is far cheaper than using separate cables for separate calls. Specifically, digital lines on fiber is used. Analogue systems used a technique called frequency division multiplexing (FDM) to do this.
The local loop:
The subscriber hand sets are powered by a battery bank in the exchange. With echo suppressors, the transmission is half duplex. With echo cancellers, it is possible to have full duplex communication. Since local loop is still analogue, we need modems for sending digital data. Since one bit is used for control purposes, we usually get 56kbps speed. Depending on the line condition, modems may automatically negotiate a lower speed.
The subscriber hand sets are powered by a battery bank in the exchange. With echo suppressors, the transmission is half duplex. With echo cancellers, it is possible to have full duplex communication. Since local loop is still analogue, we need modems for sending digital data. Since one bit is used for control purposes, we usually get 56kbps speed. Depending on the line condition, modems may automatically negotiate a lower speed.
Signaling:
Signaling refers to the information exchanges between terminal devices, exchanges and routers for setting up circuits, termination, billing, advanced network services etc. In common Channel signaling which is in band, some of the bits in the frame is used for this purpose, in which is SS7 is considered standard. Whether In band or Out of band, logically the switch controllers maybe considered to be an overlay network in the control plane. Out of band signaling (CCIS – Common Channel Interoffice Signaling) is more flexible as it allows arbitrarily complex message transfer, as they do not interfere with the regular channel.
Signaling refers to the information exchanges between terminal devices, exchanges and routers for setting up circuits, termination, billing, advanced network services etc. In common Channel signaling which is in band, some of the bits in the frame is used for this purpose, in which is SS7 is considered standard. Whether In band or Out of band, logically the switch controllers maybe considered to be an overlay network in the control plane. Out of band signaling (CCIS – Common Channel Interoffice Signaling) is more flexible as it allows arbitrarily complex message transfer, as they do not interfere with the regular channel.
Control Plane Protocol Stack in SS7:
- Application Service Element (ASE) – Application level functionality such as interpreting signaling messages. Transaction Capabilities Application Part(TCAP) allows system to invoke procedure calls on remote machines.
- Message Transfer Part 1 (MTP-1) – it is physical bit transfer usually on a digital line like E1. One of the main application of SS7 is Telephone User Part (TUP) which is responsible for setting up voice calls. The TUP interprets dialed digits, routes, reserves resources, maintains accounts etc.
Digital Technology in Telephone Networks:
Over the past 30 years, much of the traditional analogue telephone network has been replaced by digital technology. A device called codec (coder/decoder) is used to convert analogue voice signals into digital information that can be handled by the digital technology. The codec is also used to convert the digital signals back into analogue voice signals that can be handled by the older analogue technology.
Over the past 30 years, much of the traditional analogue telephone network has been replaced by digital technology. A device called codec (coder/decoder) is used to convert analogue voice signals into digital information that can be handled by the digital technology. The codec is also used to convert the digital signals back into analogue voice signals that can be handled by the older analogue technology.
Only the local loop is still analogue and this loop can be replaced by Integrated Services Digital Network (ISDN) connections. It was envisaged as an end to end digital service. Home users would be connected by same Cat3 cable. the digital bit streams are time multiplexed. The system uses Out of band signalling and uses the D channel for that. NT1 is a network terminating device which connects to the ISDN exchange on one side and a local passive bus on the other from which up to eight terminal devices can hang. ISDN turned out to be very expensive and obsolete even before the standard was finalized. The vision of broadband ISDN was sought to be realized by ATM.
Digital Subscriber Loop:
The next attempt for converting the analog local loop went in two directions:
The next attempt for converting the analog local loop went in two directions:
- Large users could be serviced by taking fiber to their premises which could terminate on an integrated digital outlet.
- The market for small users was driven by the demand for more bandwidth from the subscriber for Internet connection over the same Cat3 cable.
Computer Network | Access networks
An access network is a type of network which physically connects an end system to the immediate router (also known as the “edge router”) on a path from the end system to any other distant end system. Examples of access networks are ISP, home networks, enterprise networks, ADSL, mobile network, FITH etc.
Types of access networks:
- Ethernet –
It is the most commonly installed wired LAN technology and it provides services on the Physical and Data Link Layer of OSI reference model. Ethernet LAN typically uses coaxial cable or twisted pair wires. - DSL –
DSL stands for Digital Subscriber Line and DSL brings a connection into your home through telephone lines and a DSL line can carry both data and voice signals and the data part of the line is continuously connected. In DSL you are able to use the Internet and make phone calls simultaneously. DSL modem uses the telephone lines to exchange data with digital subscriber line access multiplexer (DSLAMs). In DSL we get 24 Mbps downstream and 2.5 Mbps upstream. - FTTH –
Fiber to the home (FTTH) uses optical fiber from a central Office (CO) directly to individual buildings and it provides high-speed Internet access among all access networks.It ensures high initial investment but lesser future investment and it is the most expensive and most future-proof option amongst all these access networks. - Wireless LANs –
It links two or more devices using wireless communication within a range. It uses high-frequency radio waves and often include an access point for connecting to the Internet. - 3G and LTE –
It uses cellular telephony to send or receive packets through a nearby base station operated by the cellular network provider. The term “3G internet” refers to the third generation of mobile phone standards as set by the International Telecommunications Union (ITU). Long Term Evolution (LTE) offers high-speed wireless communication for mobile devices and increased network capacity.
Computer Network | TCP/IP Model
Prerequisite – Layers of OSI Model
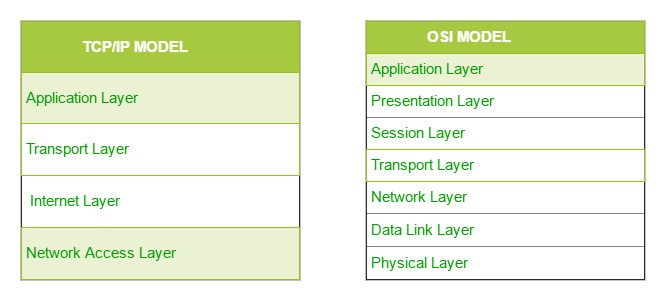
The OSI Model we just looked at is just a reference/logical model. It was designed to describe the functions of the communication system by dividing the communication procedure into smaller and simpler components. But when we talk about the TCP/IP model, it was designed and developed by Department of Defense (DoD) in 1960s and is based on standard protocols. It stands for Transmission Control Protocol/Internet Protocol. The TCP/IP model is a concise version of the OSI model. It contains four layers, unlike seven layers in the OSI model. The layers are:
- Process/Application Layer
- Host-to-Host/Transport Layer
- Internet Layer
- Network Access/Link Layer
The diagrammatic comparison of the TCP/IP and OSI model is as follows :

Difference between TCP/IP and OSI Model:
| TCP/IP | OSI |
|---|---|
| TCP refers to Transmission Control Protocol. | OSI refers to Open Systems Interconnection. |
| TCP/IP has 4 layers. | OSI has 7 layers. |
| TCP/IP is more reliable | OSI is less reliable |
| TCP/IP does not have very strict boundaries. | OSI has strict boundaries |
| TCP/IP follow a horizontal approach. | OSI follows a vertical approach. |
| TCP/IP uses both session and presentation layer in the application layer itself. | OSI uses different session and presentation layers. |
| TCP/IP developed protocols then model. | OSI developed model then protocol. |
The first layer is the Process layer on the behalf of the sender and Network Access layer on the behalf of the receiver. During this article, we will be talking on the behalf of the receiver.
1. Network Access Layer –
This layer corresponds to the combination of Data Link Layer and Physical Layer of the OSI model. It looks out for hardware addressing and the protocols present in this layer allows for the physical transmission of data.
We just talked about ARP being a protocol of Internet layer, but there is a conflict about declaring it as a protocol of Internet Layer or Network access layer. It is described as residing in layer 3, being encapsulated by layer 2 protocols.
We just talked about ARP being a protocol of Internet layer, but there is a conflict about declaring it as a protocol of Internet Layer or Network access layer. It is described as residing in layer 3, being encapsulated by layer 2 protocols.
2. Internet Layer –
This layer parallels the functions of OSI’s Network layer. It defines the protocols which are responsible for logical transmission of data over the entire network. The main protocols residing at this layer are :
- IP – stands for Internet Protocol and it is responsible for delivering packets from the source host to the destination host by looking at the IP addresses in the packet headers. IP has 2 versions:
IPv4 and IPv6. IPv4 is the one that most of the websites are using currently. But IPv6 is growing as the number of IPv4 addresses are limited in number when compared to the number of users. - ICMP – stands for Internet Control Message Protocol. It is encapsulated within IP datagrams and is responsible for providing hosts with information about network problems.
- ARP – stands for Address Resolution Protocol. Its job is to find the hardware address of a host from a known IP address. ARP has several types: Reverse ARP, Proxy ARP, Gratuitous ARP and Inverse ARP.
3. Host-to-Host Layer –
This layer is analogous to the transport layer of the OSI model. It is responsible for end-to-end communication and error-free delivery of data. It shields the upper-layer applications from the complexities of data. The two main protocols present in this layer are :
- Transmission Control Protocol (TCP) – It is known to provide reliable and error-free communication between end systems. It performs sequencing and segmentation of data. It also has acknowledgment feature and controls the flow of the data through flow control mechanism. It is a very effective protocol but has a lot of overhead due to such features. Increased overhead leads to increased cost.
- User Datagram Protocol (UDP) – On the other hand does not provide any such features. It is the go-to protocol if your application does not require reliable transport as it is very cost-effective. Unlike TCP, which is connection-oriented protocol, UDP is connectionless.
- HTTP and HTTPS – HTTP stands for Hypertext transfer protocol. It is used by the World Wide Web to manage communications between web browsers and servers. HTTPS stands for HTTP-Secure. It is a combination of HTTP with SSL(Secure Socket Layer). It is efficient in cases where the browser need to fill out forms, sign in, authenticate and carry out bank transactions.
- SSH – SSH stands for Secure Shell. It is a terminal emulations software similar to Telnet. The reason SSH is more preferred is because of its ability to maintain the encrypted connection. It sets up a secure session over a TCP/IP connection.
- NTP – NTP stands for Network Time Protocol. It is used to synchronize the clocks on our computer to one standard time source. It is very useful in situations like bank transactions. Assume the following situation without the presence of NTP. Suppose you carry out a transaction, where your computer reads the time at 2:30 PM while the server records it at 2:28 PM. The server can crash very badly if it’s out of sync.
4. Process Layer –
This layer performs the functions of top three layers of the OSI model: Application, Presentation and Session Layer. It is responsible for node-to-node communication and controls user-interface specifications. Some of the protocols present in this layer are: HTTP, HTTPS, FTP, TFTP, Telnet, SSH, SMTP, SNMP, NTP, DNS, DHCP, NFS, X Window, LPD. Have a look at Protocols in Application Layer for some information about these protocols. Protocols other than those present in the linked article are :
Computer Network | Layers of OSI Model
Prerequisite : Basics of Computer Networking
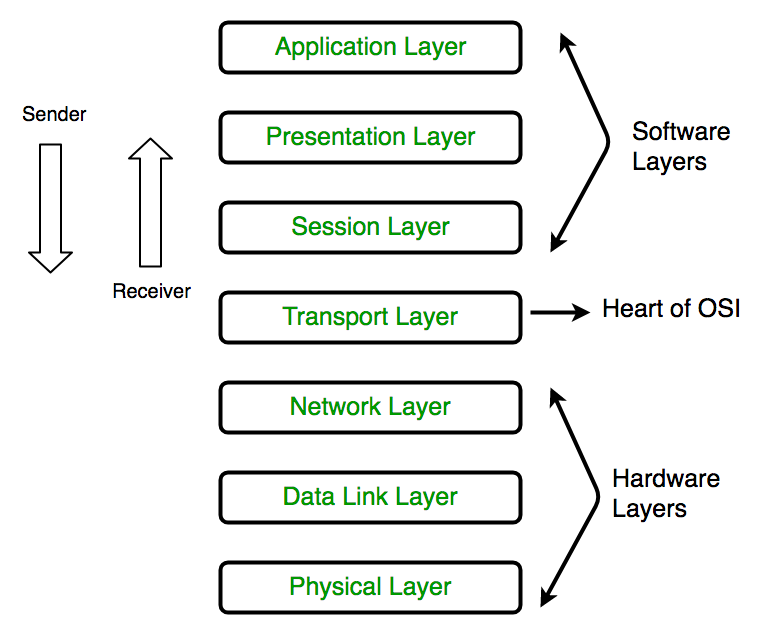
OSI stands for Open Systems Interconnection. It has been developed by ISO – ‘International Organization of Standardization‘, in the year 1974. It is a 7 layer architecture with each layer having specific functionality to perform. All these 7 layers work collaboratively to transmit the data from one person to another across the globe.

1. Physical Layer (Layer 1) :
The lowest layer of the OSI reference model is the physical layer. It is responsible for the actual physical connection between the devices. The physical layer contains information in the form of bits. It is responsible for the actual physical connection between the devices. When receiving data, this layer will get the signal received and convert it into 0s and 1s and send them to the Data Link layer, which will put the frame back together.
The functions of the physical layer are :
- Bit synchronization: The physical layer provides the synchronization of the bits by providing a clock. This clock controls both sender and receiver thus providing synchronization at bit level.
- Bit rate control: The Physical layer also defines the transmission rate i.e. the number of bits sent per second.
- Physical topologies: Physical layer specifies the way in which the different, devices/nodes are arranged in a network i.e. bus, star or mesh topolgy.
- Transmission mode: Physical layer also defines the way in which the data flows between the two connected devices. The various transmission modes possible are: Simplex, half-duplex and full-duplex.
* Hub, Repeater, Modem, Cables are Physical Layer devices.
** Network Layer, Data Link Layer and Physical Layer are also known as Lower Layers or Hardware Layers.
** Network Layer, Data Link Layer and Physical Layer are also known as Lower Layers or Hardware Layers.
2. Data Link Layer (DLL) (Layer 2) :
The data link layer is responsible for the node to node delivery of the message. The main function of this layer is to make sure data transfer is error free from one node to another, over the physical layer. When a packet arrives in a network, it is the responsibility of DLL to transmit it to the Host using its MAC address.
Data Link Layer is divided into two sub layers :
Data Link Layer is divided into two sub layers :
- Logical Link Control (LLC)
- Media Access Control (MAC)
The packet received from Network layer is further divided into frames depending on the frame size of NIC(Network Interface Card). DLL also encapsulates Sender and Receiver’s MAC address in the header.
The Receiver’s MAC address is obtained by placing an ARP(Address Resolution Protocol) request onto the wire asking “Who has that IP address?” and the destination host will reply with its MAC address.

The functions of the data Link layer are :
The functions of the data Link layer are :
- Framing: Framing is a function of the data link layer. It provides a way for a sender to transmit a set of bits that are meaningful to the receiver. This can be accomplished by attaching special bit patterns to the beginning and end of the frame.
- Physical addressing: After creating frames, Data link layer adds physical addresses (MAC address) of sender and/or receiver in the header of each frame.
- Error control: Data link layer provides the mechanism of error control in which it detects and retransmits damaged or lost frames.
- Flow Control: The data rate must be constant on both sides else the data may get corrupted thus , flow control coordinates that amount of data that can be sent before receiving acknowledgement.
- Access control: When a single communication channel is shared by multiple devices, MAC sub-layer of data link layer helps to determine which device has control over the channel at a given time.
* Packet in Data Link layer is referred as Frame.
** Data Link layer is handled by the NIC (Network Interface Card) and device drivers of host machines.
*** Switch & Bridge are Data Link Layer devices.
** Data Link layer is handled by the NIC (Network Interface Card) and device drivers of host machines.
*** Switch & Bridge are Data Link Layer devices.
3. Network Layer (Layer 3) :
Network layer works for the transmission of data from one host to the other located in different networks. It also takes care of packet routing i.e. selection of the shortest path to transmit the packet, from the number of routes available. The sender & receiver’s IP address are placed in the header by network layer.
The functions of the Network layer are :
The functions of the Network layer are :
- Routing: The network layer protocols determine which route is suitable from source to destination. This function of network layer is known as routing.
- Logical Addressing: In order to identify each device on internetwork uniquely, network layer defines an addressing scheme. The sender & receiver’s IP address are placed in the header by network layer. Such an address distinguishes each device uniquely and universally.
* Segment in Network layer is referred as Packet.

** Network layer is implemented by networking devices such as routers.
** Network layer is implemented by networking devices such as routers.
4. Transport Layer (Layer 4) :
Transport layer provides services to application layer and takes services from network layer. The data in the transport layer is referred to as Segments. It is responsible for the End to End delivery of the complete message. Transport layer also provides the acknowledgment of the successful data transmission and re-transmits the data if an error is found.
• At sender’s side:
Transport layer receives the formatted data from the upper layers, performs Segmentation and also implements Flow & Error control to ensure proper data transmission. It also adds Source and Destination port number in its header and forwards the segmented data to the Network Layer.
Note: The sender need to know the port number associated with the receiver’s application.
Generally, this destination port number is configured, either by default or manually. For example, when a web application makes a request to a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default port assigned.
• At receiver’s side:
Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
• At sender’s side:
Transport layer receives the formatted data from the upper layers, performs Segmentation and also implements Flow & Error control to ensure proper data transmission. It also adds Source and Destination port number in its header and forwards the segmented data to the Network Layer.
Note: The sender need to know the port number associated with the receiver’s application.
Generally, this destination port number is configured, either by default or manually. For example, when a web application makes a request to a web server, it typically uses port number 80, because this is the default port assigned to web applications. Many applications have default port assigned.
• At receiver’s side:
Transport Layer reads the port number from its header and forwards the Data which it has received to the respective application. It also performs sequencing and reassembling of the segmented data.
The functions of the transport layer are :
- Segmentation and Reassembly: This layer accepts the message from the (session) layer , breaks the message into smaller units . Each of the segment produced has a header associated with it. The transport layer at the destination station reassembles the message.
- Service Point Addressing: In order to deliver the message to correct process, transport layer header includes a type of address called service point address or port address. Thus by specifying this address, transport layer makes sure that the message is delivered to the correct process.
The services provided by transport layer :
- Connection Oriented Service: It is a three-phase process which include
– Connection Establishment
– Data Transfer
– Termination / disconnection
In this type of transmission, the receiving device sends an acknowledgment, back to the source after a packet or group of packet is received. This type of transmission is reliable and secure. - Connection less service: It is a one phase process and includes Data Transfer. In this type of transmission, the receiver does not acknowledge receipt of a packet. This approach allows for much faster communication between devices. Connection oriented Service is more reliable than connection less Service.
* Data in the Transport Layer is called as Segments.
** Transport layer is operated by the Operating System. It is a part of the OS and communicates with the Application Layer by making system calls.
Transport Layer is called as Heart of OSI model.
** Transport layer is operated by the Operating System. It is a part of the OS and communicates with the Application Layer by making system calls.
Transport Layer is called as Heart of OSI model.
5. Session Layer (Layer 5) :
This layer is responsible for establishment of connection, maintenance of sessions, authentication and also ensures security.
The functions of the session layer are :
The functions of the session layer are :
- Session establishment, maintenance and termination: The layer allows the two processes to establish, use and terminate a connection.
- Synchronization : This layer allows a process to add checkpoints which are considered as synchronization points into the data. These synchronization point help to identify the error so that the data is re-synchronized properly, and ends of the messages are not cut prematurely and data loss is avoided.
- Dialog Controller : The session layer allows two systems to start communication with each other in half-duplex or full-duplex.
**All the below 3 layers(including Session Layer) are integrated as a single layer in TCP/IP model as “Application Layer”.
**Implementation of these 3 layers is done by the network application itself. These are also known as Upper Layers or Software Layers.
**Implementation of these 3 layers is done by the network application itself. These are also known as Upper Layers or Software Layers.
SCENARIO:
Let’s consider a scenario where a user wants to send a message through some Messenger application running in his browser. The “Messenger” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, encrypted (if any secure data) and converted into bits (0’s and 1’s) so that it can be transmitted.

Let’s consider a scenario where a user wants to send a message through some Messenger application running in his browser. The “Messenger” here acts as the application layer which provides the user with an interface to create the data. This message or so-called Data is compressed, encrypted (if any secure data) and converted into bits (0’s and 1’s) so that it can be transmitted.

6. Presentation Layer (Layer 6) :
Presentation layer is also called the Translation layer.The data from the application layer is extracted here and manipulated as per the required format to transmit over the network.
The functions of the presentation layer are :
The functions of the presentation layer are :
- Translation : For example, ASCII to EBCDIC.
- Encryption/ Decryption : Data encryption translates the data into another form or code. The encrypted data is known as the cipher text and the decrypted data is known as plain text. A key value is used for encrypting as well as decrypting data.
- Compression: Reduces the number of bits that need to be transmitted on the network.
7. Application Layer (Layer 7) :
At the very top of the OSI Reference Model stack of layers, we find Application layer which is implemented by the network applications. These applications produce the data, which has to be transferred over the network. This layer also serves as a window for the application services to access the network and for displaying the received information to the user.
Ex: Application – Browsers, Skype Messenger etc.
**Application Layer is also called as Desktop Layer.
 The functions of the Application layer are :
The functions of the Application layer are :
Ex: Application – Browsers, Skype Messenger etc.
**Application Layer is also called as Desktop Layer.
- Network Virtual Terminal
- FTAM-File transfer access and management
- Mail Services
- Directory Services
OSI model acts as a reference model and is not implemented in Internet because of its late invention. Current model being used is the TCP/IP model.
Introduction to Active Directory Domain Services
A directory is a hierarchical structure that stores information about objects on the network. A directory, in the most generic sense, is a comprehensive listing of objects. A phone book is a type of directory that stores information about people, businesses, and government organizations. Phone books typically record names, addresses, and phone numbers.
Active Directory (AD) is a Microsoft technology used to manage computers and other devices on a network. It is a primary feature of Windows Server, an operating system that runs both local and Internet-based servers.
Benefits of Active Directory –
- Hierarchical organizational structure.
- Multimaster Authentication & Multimaster replication (the ability to access and modify AD DS from multiple
points of administration) - A single point of acess to network resources.
- Ability to create trust relationships with external networks running preious versions of Active Directory and even Unix.
Directory Service –
A directory service is a hierarchical arrangement of objects which are structured in a way that makes access easy. However, functioning as a locator service is not AD’s exclusive purpose. It also helps organizations have a central administration over all the activities carried out in their networks. Essentially a Network Directory Service:
A directory service is a hierarchical arrangement of objects which are structured in a way that makes access easy. However, functioning as a locator service is not AD’s exclusive purpose. It also helps organizations have a central administration over all the activities carried out in their networks. Essentially a Network Directory Service:
- Provides information about the user objects, computers and services in the network.
- Stores this information in a secure database and provides tools to manage and search the directory.
- Allows to manage the user accounts and resources, apply policies consistently as needed by an organization.
Active Directory provides several different services, which fall under the umbrella of “Active Directory Domain Services, ” or AD DS. These services include:
- Domain Services –
Stores centralized data and manages communication between users and domains; includes login authentication and search functionality - Certificate Services –
It generates, manages and shares certificates. A certificate uses encryption to enable a user to exchange information over the internet securely with a public key. - Lightweight Directory Services –
Supports directory-enabled applications using the open (LDAP) protocol. - Directory Federation Services –
Provides single-sign-on (SSO) to authenticate a user in multiple web applications in a single session. - Rights Management –
It controls information rights and management. AD RMS encrypts content, such as email or Word documents, on a server to limit access.
Domain Controllers –
A server that is running AD DS is called a domain controller.Domain controllers host and replicate the directory service database inside the forest. The directory service also provides services for managing and authenticating resources in the forest.These servers host essential services in AD DS, including the following:
– Kerberos Key Distribution Center (kdc)
– NetLogon (Netlogon)
– Windows Time (W32time)
– Intersite Messaging (IsmServ)
A server that is running AD DS is called a domain controller.Domain controllers host and replicate the directory service database inside the forest. The directory service also provides services for managing and authenticating resources in the forest.These servers host essential services in AD DS, including the following:
– Kerberos Key Distribution Center (kdc)
– NetLogon (Netlogon)
– Windows Time (W32time)
– Intersite Messaging (IsmServ)
Active Directory Objects:
- Container Objects –
These objects can contain other objects inside them, and we can make collection from them. For Ex- Forest, Tree, Domains, Organisational Units. - Leaf Objects –
These objects can not contain other objects inside them. For Ex- users, computers, printers, etc. Common Terminologies and Active Directory Concepts:
Common Terminologies and Active Directory Concepts:- Schema –
A set of rules, the schema, that defines the classes of objects and attributes contained in the directory, the constraints and limits on instances of these objects, and the format of their names. - Global catalog –
A global catalog that contains information about every object in the directory. This allows users and administrators to find directory information regardless of which domain in the directory actually contains the data. For more information about the global catalog, see The role of the global catalog. - Forest Root Domain –
The first domain that is installed in an Active Directory Forest is referred to as the root domain. - Sites –
Sites in AD DS represent the physical structure, or topology, of your network. AD DS uses network topology information, which is stored in the directory as site, subnet, and site link objects, to build
the most efficient replication topology. - Lightweight Directory Access Protocol –
AD is based on the Lightweight Directory Access Protocol (LDAP). This protocol provides a common language for clients and servers to speak to one another.
- Schema –
Advantages and Disadvantages of Computer Networking
Computer network is defined as a set of interconnected autonomous systems that facilitate distributed processing of information. It results in better performance with high speed of processing.
Advantages of Network:
These are main advantages of Computer Networks:
These are main advantages of Computer Networks:
- Central Storage of Data –
Files can be stored on a central node (the file server) that can be shared and made available to each and every user in an organization. - Anyone can connect to a computer network –
There is a negligible range of abilities required to connect to a modern computer network. The effortlessness of joining makes it workable for even youthful kids to start exploiting the data. - Faster Problem solving –
Since an extensive procedure is disintegrated into a few littler procedures and each is taken care of by all the associated gadgets, an explicit issue can be settled in lesser time. - Reliability –
Reliability implies backing up of information. Due to some reason equipment crash, and so on, the information gets undermined or inaccessible on one PC, another duplicate of similar information is accessible on another workstation for future use, which prompts smooth working and further handling without interruption. - It is highly flexible –
This innovation is known to be truly adaptable, as it offers clients the chance to investigate everything about fundamental things, for example, programming without influencing their usefulness. - Security through Authorization –
Security and protection of information is additionally settled through system. As just the system clients are approved to get to specific records or applications, no other individual can crack the protection or security of information. - It boosts storage capacity –
Since you will share data, records and assets to other individuals, you need to guarantee all information and substance are legitimately put away in the framework. With this systems administration innovation, you can do the majority of this with no issue, while having all the space you requirement for capacity.
Disadvantages of Network:
These are main disadvantages of Computer Networks:
These are main disadvantages of Computer Networks:
- It lacks robustness –
If a PC system’s principle server separates, the whole framework would end up futile. Also, if it has a bridging device or a central linking server that fails, the entire network would also come to a standstill. To manage these issues, gigantic systems ought to have a ground-breaking PC to fill in as document server to influence setting to up and keeping up the system less demanding. - It lacks independence –
PC organizing includes a procedure that is worked utilizing PCs, so individuals will depend a greater amount of PC work, rather than applying an exertion for their jobs that needs to be done. Beside this, they will be subject to the primary document server, which implies that, in the event that it separates, the framework would end up futile, making clients inactive. - Virus and Malware –
On the off chance that even one PC on a system gets contaminated with an infection, there is a possibility for alternate frameworks to get tainted as well. Infections can spread on a system effectively, in view of the between availability of different gadgets.4. Lack of Independence - Cost of network –
The expense of executing the system including cabling and equipment can be expensive.
PC systems administration will dependably be a quick and advantageous methods for exchanging and sharing data, yet individuals ought to know about its outcomes too.







tcp/ip model
ReplyDeleteVery informative. Now I got an idea about this topic. thanks for the content.
ReplyDeleteCCNA Training In Chennai
CCNA Training Online
CCNA Course In Coimbatore